Out of the box, nearly all operating systems are configured insecurely. The idea of OS hardening is to minimise a computer's exposure to current and future threats by fully configuring the operating system and removing unnecessary applications.
WHAT IS SYSTEMS HARDENING?
Systems hardening is a collection of tools, techniques, and best practices to reduce vulnerability in technology applications, systems, infrastructure, firmware, and other areas. The goal of system hardening is to reduce security risk by eliminating potential attack vectors and condensing the system’s attack surface. By removing superfluous programmes, account functions, applications, ports, permissions, access, etc., attackers and malware have fewer opportunities to gain a foothold within your IT ecosystem.
Systems hardening demands a methodical approach to auditing, identifying, closing, and controlling potential security vulnerabilities throughout your organization. There are several types of system hardening activities, including:
• Application hardening
• Operating system hardening
• Server hardening
• Endpoint hardening
• Database hardening
• Network hardening
Although the principles of system hardening are universal, specific tools and techniques do vary depending on the type of hardening you are carrying out. System hardening is needed throughout the lifecycle of technology, from initial installation through configuration, maintenance, and support to end-of-life decommissioning. Systems hardening is also a requirement of mandates such as PCI DSS and HIPAA and is increasingly demanded by cyber insurers.
• Default and hardcoded passwords
• Passwords and other credentials stored in plain text files
• Unpatched software and firmware vulnerabilities
• Poorly configured BIOS, firewalls, ports, servers, switches, routers, or other parts of the infrastructure
• Unencrypted network traffic or data at rest
• Lack, or deficiency, of privileged access controls
HOW DO YOU HARDEN A SYSTEM?
You harden a system by reducing the “attack surface." The combination of all the potential flaws and backdoors in technology can be exploited by threat actors. These vulnerabilities can occur in many ways. Common attack surface vulnerabilities include:
Default passwords: Attackers can leverage automated password crackers to guess the defaults. The attack surface this presents could be large if the same defaults are used across many different endpoints—from desktops to IoT—or accounts.
Hardcoded passwords and other credentials stored in plain text files can increase the attack surface in a couple important ways. If they are forgotten in deployed code or otherwise publicly exposed, the hardcoded credentials can provide a backdoor into the organization.
Unpatched software and firmware vulnerabilities are historically one of the biggest contributors to attack surfaces. While patching will mitigate a vulnerability, patches are not always available, as in the case of zero-day threats. Moreover, some patches may be too disruptive to implement or not economically feasible.
Lack, or deficiency, of privileged access controls With the expansion of the cloud and all things digital, privileged accounts and access have exploded. The privileged account attack surface is not just humans and employees but also increasingly involves machines and vendors. In cloud environments, privileged access and accounts may be dynamic and ephemeral, further complicating efforts to gain visibility and control over this massive risk.
Poorly configured BIOS, firewalls, ports, servers, switches, routers, or other parts of the infrastructure With the strong growth in cloud and hybrid infrastructure, IT environments are becoming increasingly complex. This complexity is fertile ground for misconfigurations, which can not only cause systems to crash or misfire but also create dangerous security holes. Misconfigurations have resulted in some of the worst cloud breaches in recent years, such as by inadvertently exposing data buckets or providing publicly accessible backdoors to critical infrastructure.
Unencrypted, or inadequately encrypted, network traffic or data at rest can make it easy for attackers to access data or eavesdrop on conversations and potentially gain important information (such as passwords) needed to advance an attack.
Additionally, the Centre for Internet Security (CIS) maintains updated guidelines on their site around best practice system configurations for specific use cases. The CIS Benchmarks include over 100 guidelines across 25 vendor product families (Amazon Linux, Amazon AWS, Apple iOS, Apple macOS, Checkpoint Firewall, Cisco, Docker, Google Cloud, Microsoft Azure, etc.).
10 BEST PRACTICES FOR SYSTEMS HARDENING
The type of hardening you carry out depends on the risks in your existing technology, the resources you have available, and the priority for making fixes.
1. Audit your existing systems: Carry out a comprehensive audit of your existing technology (which you can use). Use penetration testing, vulnerability scanning, configuration management, and other security auditing tools to find flaws in the system and prioritise fixes. Conduct system hardening assessments against resources using industry standards from NIST, Microsoft, CIS, DISA, etc.
2. Create a strategy for system hardening. You do not need to harden all of your systems at once. Instead, create a strategy and plan based on risks identified within your technology ecosystem and use a phased approach to remediate the biggest flaws.
3. Patch vulnerabilities immediately. Ensure you have an automated and comprehensive vulnerability identification and patching system in place. Systematically identify vulnerabilities and prioritise remediation. In some instances, vulnerabilities cannot be patched. In these instances, ensure there are other mitigations in place, such as removing admin rights, which many exploiters need in order to exploit a vulnerability, and/or having cyber insurance in place.
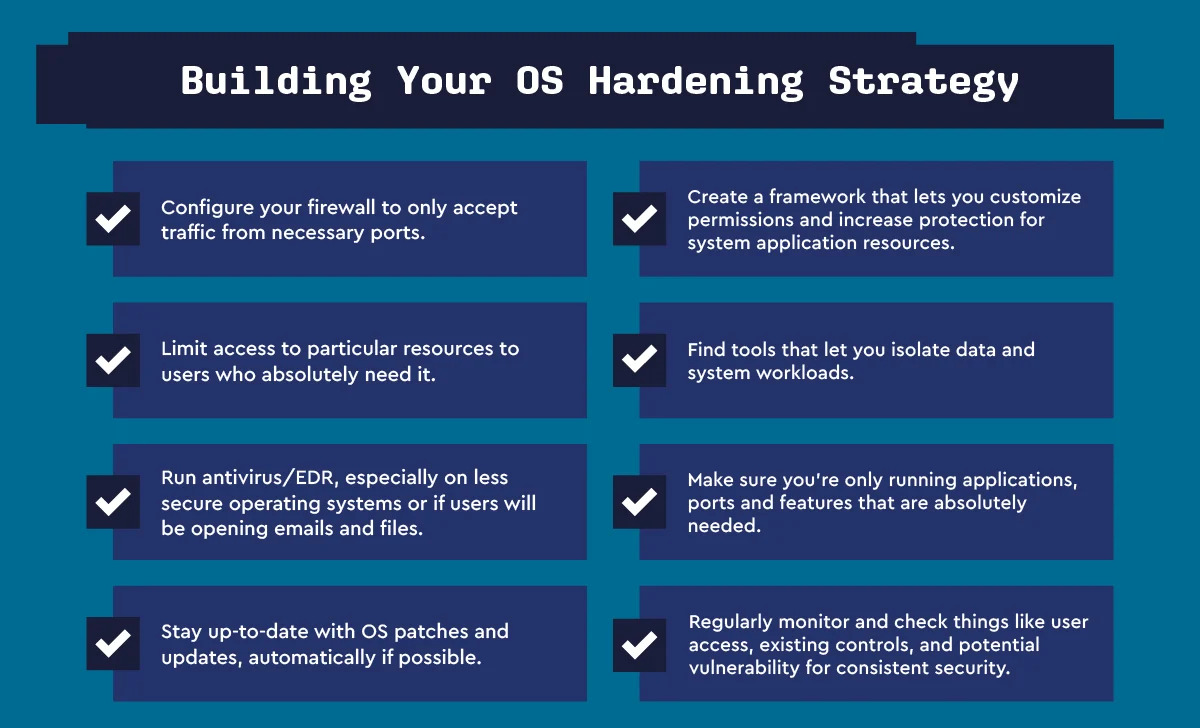
4. Network hardening: Ensure your firewall is properly configured and all rules are regularly audited; secure remote access points and users; block any unused or unneeded open network ports; disable and remove unnecessary protocols and services; implement access lists; and encrypt network traffic.
5. Server hardening: Put all company-hosted servers in a secure datacenter; never test hardening on production servers; always harden servers before connecting them to the internet or external networks; avoid installing unnecessary software on a server; segregate servers appropriately; ensure superuser and administrative shares are properly set up; and limit rights and access in line with the principle of least privilege. In cloud environments, it is also particularly important to reduce port exposure so data is not inadvertently leaked or backdoor access is provided to infrastructure.
6. Endpoint hardening: Remove local admin rights on all Windows and macOS endpoints. Ensure no workstations, laptops, or IoT devices have default passwords. Remove any unneeded software and block any unnecessary communications.
7. Application hardening: remove any components or functions you do not need; restrict access to applications based on user roles and context (such as with application control); remove all sample files and default passwords. Application passwords should then be managed via an application password management/privileged password management solution that enforces password best practices (password rotation, length, etc.). Hardening of applications should also entail inspecting integrations with other applications and systems and removing or reducing unnecessary integration components and privileges.
8.Database hardening: create admin restrictions, such as by controlling privileged access, on what users can do in a database; turn on node checking to verify applications and users; encrypt database information—both in transit and at rest; enforce secure passwords; introduce role-based access control (RBAC) privileges; remove unused accounts;
9. Operating system hardening: apply OS updates, service packs, and patches automatically; remove unnecessary drivers, file sharing, libraries, software, services, and functionality; encrypt local storage; tighten registry and other system permissions; log all activity, errors, and warnings; implement privileged user controls.
10. Eliminate unnecessary accounts and privileges. Enforce least privilege by removing unnecessary accounts (such as orphaned accounts and unused accounts) and privileges throughout your IT infrastructure. This is one of the most powerful security practices for reducing the attack surface.
HARDENING STRATEGY
BENEFITS OF SYSTEMS HARDENING
Systems hardening requires continuous effort, but the diligence will pay off in substantive ways across your organisation via:
Enhanced system functionality: Since fewer programmes and less functionality means there is less risk of operational issues, misconfigurations, incompatibilities, and compromise,
Significantly improved security: A reduced attack surface translates into a lower risk of data breaches, unauthorised access, system hacking, or malware.
Simplified compliance and auditability: Fewer programmes and accounts, coupled with a less complex environment, means auditing the environment will usually be more transparent and straightforward.