Website security is very important to protect your business, brand, and reputation and also to prevent financial loss, including shutting down your business website.
WHY CHOOSE VERACITY
| Injection & Broken Authentication | Sensitive Data Exposure & XML Enternal Entities | Broken Access Control | Security Misconfiguration |
| Insecure Deserialisation | Componenets with known Vulnerabilities | Insufficient Logging & Monitoring |
HOW DO WE DIFFER
A custom security assessment project management platform will allow us to closely collaborate with security consultants to make our clients lives easier.
| Identifying detailed security issues with recommendations on realtime basis. | Client have freedom to generate report any time. | Transparent visibility on the project status. | High quality and top standard report quality to present CXO. |
| Integrated secure coding campaign for developers. | Detailed reports for all re assessments with Track. | Detailed issue track sheets with compliance mapping. |
SERVICE CAPABILITIES
Once scoping is complete, there are seven phases to be carried out:
Information Gathering / DiscoverySpecific tools will be used to obtain as much information as possible from the current internal infrastructure. | Service EnumerationAll services discovered on the hosts under test will be itemised. Service enumeration allows specific software types and versions to be retrieved from the network, as well as policies, shares, resources, and valid user accounts. |
Vulnerability AssessmentThis phase of testing will attempt to analyse the information retrieved in previous steps in order to determine whether a specific weakness exists or not. | Manual TestingOnce all of the hosts and services have been identified, manual testing techniques and follow-up will be used to either extract further sensitive information from the host or, depending on the rules of engagement, exploit it. |
Post exploitationOnce a machine's scope has been compromised, pivoting and lateral movement techniques will be exercised. This practice is often employed to fully explore and demonstrate the true risk of a vulnerability by emulating the ‘snowball’ effect of stacked vulnerabilities. | Information EgressThe routes through which data can be extracted from the systems in scope will be examined and used to identify where extra controls could be implemented or security enhanced. |
ReportingA business executive summary, high-level descriptions, and technical details of each finding are provided to offer the customer a wealth of information to implement remediation’s to not only fix the current issue but also the underlying root cause, ensuring issues of the same nature do not re-occur. |
THE BENEFITS OF A WEBSITE PENETRATION TEST
| Keep untrusted data separate from commands and queries. | Validates the effectiveness of current security safeguards. | We provide detailed remediation steps to detect existing flaws and prevent future attacks. |
| Identifies the vulnerabilities in your website and we categorized each vulnerability into Development issue, Configuration issue, Business logic issues and Missing best practices. | We quantifies the risk and gain real-world compliance and technical insight into your vulnerabilities. | We protect the integrity of assets in case of existing malicious code hidden in any of them. |
WEBSITE PENETRATION TESTING
If you have assets of prominence or if your site puts you in the public eye, then your website calls for a security test. To safeguard your business and reputation, Veracity offers comprehensive website penetration testing services. This test helps you identify all exploitable weaknesses that are hidden in your website and secure them.
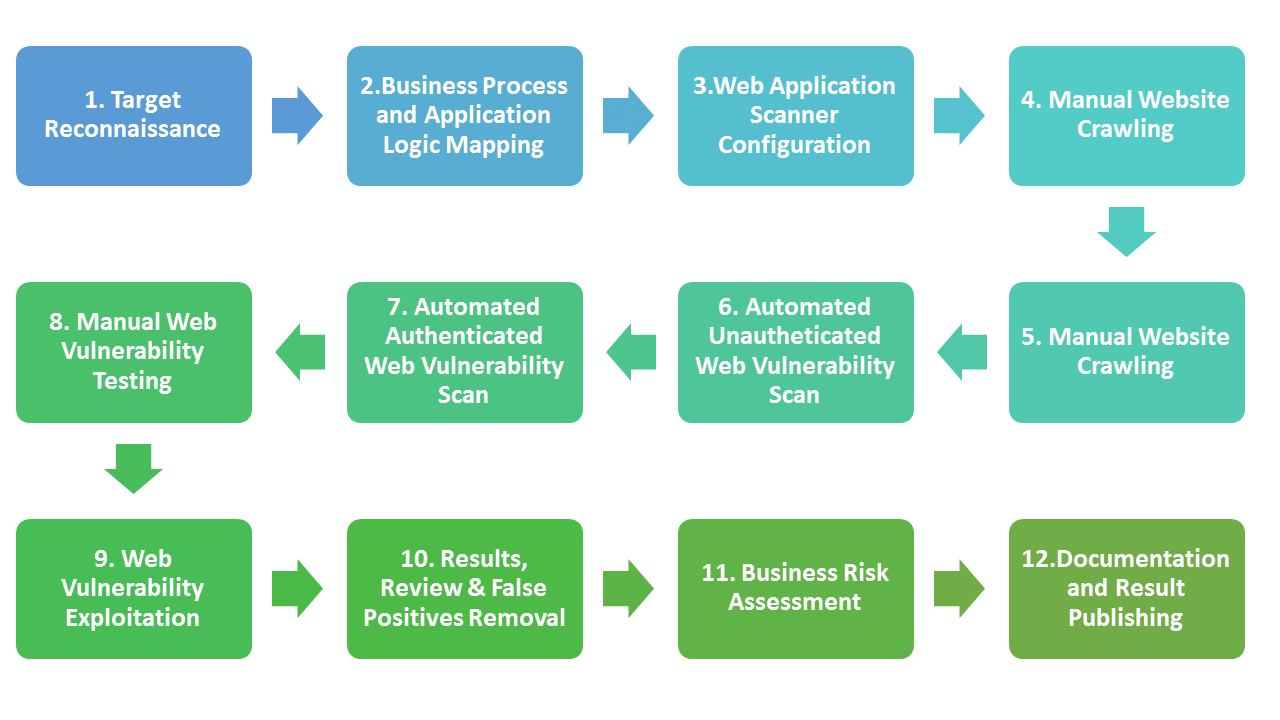
APPROACH
The verification process is tailored to fit your requirements and is highly effective in protecting your business from losing confidential and valuable information.
Standards we follow
- OWASP
- OSSTMM
- PTES
- WASC
- SANS
- NIST SP800 - 115